By Mark Clementson and Michael Johnson
From 2018 to 2023, Federal spending on cloud computing services increased by 231%, rising from $5.8 billion1 to $19.2 billion.2 Across the 24 Chief Financial Officers (CFO) Act agencies, the number of cloud system authorizations increased by approximately 60%.3 As agencies continue to invest and transition to cloud computing, it is important to understand the cloud, security implications, and how it impacts an audit.
What is the Cloud?
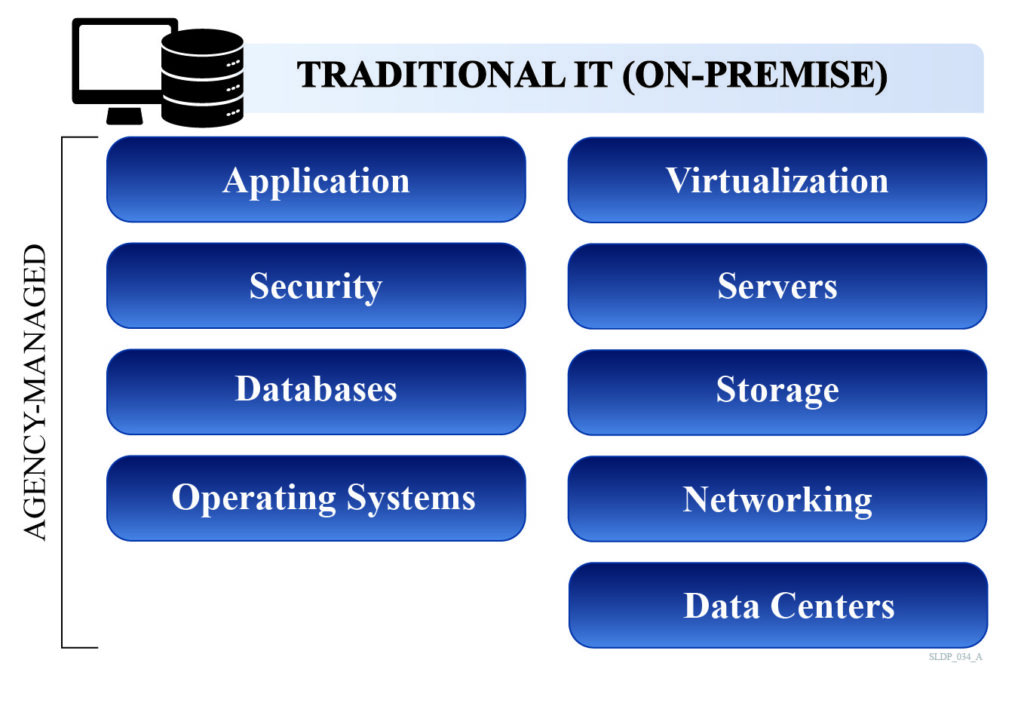 Cloud computing is a transition from traditional, on-premises management of information systems to a virtual environment. In traditional management, an agency owns, manages, and maintains all computing resources on-premises, including the networks, servers, storage, applications, and services. The traditional approach is akin to building a house: agencies control the construction of the house, make customizations, and are responsible for costs such as insurance, maintenance, and repairs.
Cloud computing is a transition from traditional, on-premises management of information systems to a virtual environment. In traditional management, an agency owns, manages, and maintains all computing resources on-premises, including the networks, servers, storage, applications, and services. The traditional approach is akin to building a house: agencies control the construction of the house, make customizations, and are responsible for costs such as insurance, maintenance, and repairs.
National Institute of Standards and Technology (NIST) defines five essential characteristics of cloud computing:
- On-Demand Self-Service: Agencies can manage the computing capabilities (e.g., storage) without a service representative
- Broad Network Access: The capabilities are available over the internet
- Resource Pooling: The Cloud Service Providers (CSP) uses common computing resources to serve multiple customers
- Rapid Elasticity: Computing capabilities can be scaled with demand (both expand and restrict)
- Measured Service: Usage can be monitored by both the provider and consumer.
Cloud Service Models
Cloud computing involves agencies contracting with CSPs to remotely provide computing resources over the internet. This approach eliminates the need for agencies to own and manage all computing resources. CSPs are a type of service organization that deliver cloud services. Often, elements of an organization’s financially relevant systems, if not the entire system, are hosted by CSP making it relevant to an organization’s internal controls over financial reporting..
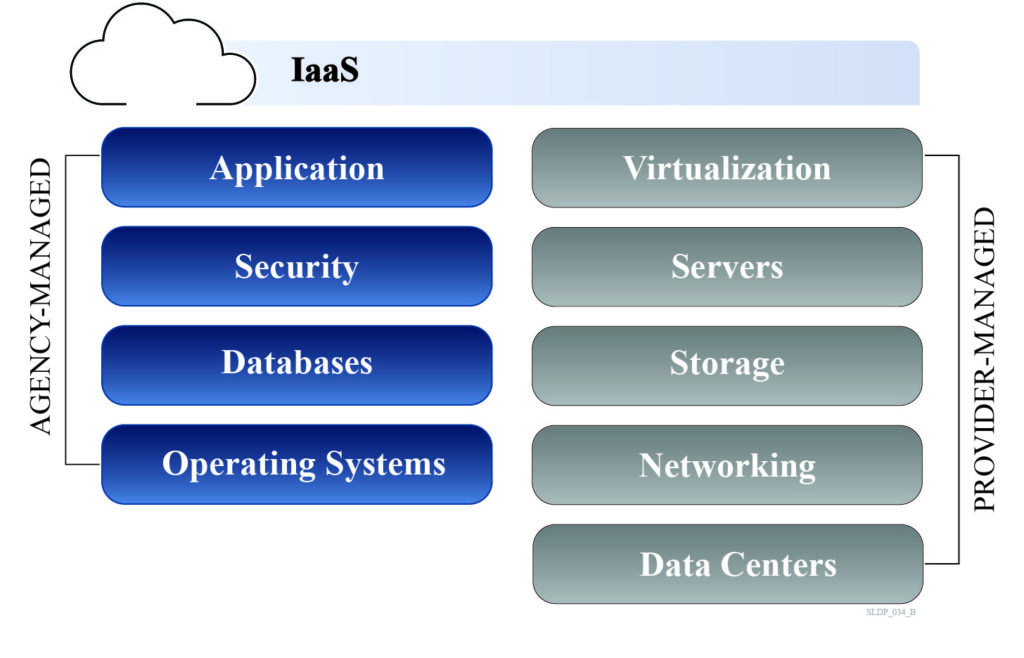
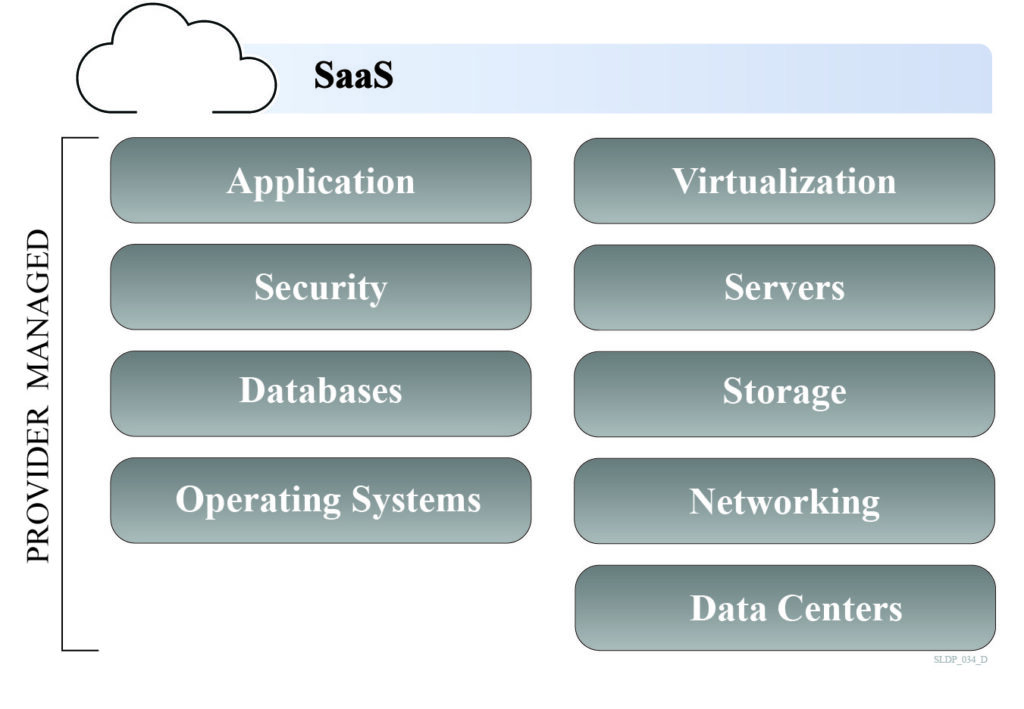
The different service models provide agencies the opportunity to balance the pros and cons of cloud computing by offering varying levels of customization and responsibilities. The cloud service model selected is used to determine an entity’s responsibilities and the applicable security control baseline in Federal Risk and Authorization Management Program (FedRAMP). There are three main service models that CSPs offer: 1) Infrastructure as a Service (IaaS); 2) Platform as a Service (PaaS); and 3) Software as a Service (SaaS). These service models offer varying levels of ownership, management, and maintenance of computing resources.
With IaaS, CSPs provide the computing infrastructure and hardware, including networking features, data storage, and servers. IaaS has the most overlap with traditional information technology (IT) environments, where agencies will outsource the hosting services. This cloud service model provides the most flexibility and management control over IT resources. IaaS is equivalent to renting a house, where an individual can pick a house according to their specifications and pay a rental fee, but also furnish and decorate the house based on their preferences. If issues arise, the landlord is responsible for fixing and maintaining the house.
With PaaS, the CSPs are responsible for all infrastructure, as well as the operating systems. Agencies are responsible for the application and may be able to control the configuration settings for the hosting environment. PaaS allows agencies to focus on developing and managing applications. PaaS is like renting a fully furnished house: the individual can pick a house with the exact specifications he/she wants, but not the type of furniture and decor. They pay a rental fee, but there is limited customization allowed. If something goes wrong with the house or any of the furniture in it, the landlord is responsible for fixing it.

With SaaS, the CSP runs and manages a complete product, generally end user applications, such as e-mail, customer relationship management, or document editing software. SaaS offers a subscription or “pay for what you use” service, where agencies are only responsible utilizing the cloud-based software. SaaS is comparable to staying at a hotel: you can select a room with your specifications, and you pay per night, but there is no customization.
Deployment Models
There are four main deployment models that may be used to deploy Cloud Services. Like the cloud service models above, the deployment models allow agencies to weigh the pros and cons of the different deployment methods. The choice of deployment model depends on the needs of the entity. Agencies must decide what fits their business needs by considering: security, business use, cost, scalability/flexibility, up time/availability, and integration.
 Private Clouds are for exclusive use by one organization. Private clouds can be owned and managed by an agency or CSP and may be maintained on- or off-premises. This option offers the greatest level of security and customization, but comes at a higher cost.
Private Clouds are for exclusive use by one organization. Private clouds can be owned and managed by an agency or CSP and may be maintained on- or off-premises. This option offers the greatest level of security and customization, but comes at a higher cost.
 A Community Cloud is for exclusive use by a community with similar missions, security requirements, etc. Community clouds can be owned and managed by an agency within the community or CSP and may be maintained on- or off-premises.
A Community Cloud is for exclusive use by a community with similar missions, security requirements, etc. Community clouds can be owned and managed by an agency within the community or CSP and may be maintained on- or off-premises.
 Public Clouds are open for use. Public clouds are owned and managed by a CSP and exist off-premises with the CSP. They come at the lowest cost and have the easiest infrastructure management; however, because of the shared resources, there are higher security risks and a lack of customization.
Public Clouds are open for use. Public clouds are owned and managed by a CSP and exist off-premises with the CSP. They come at the lowest cost and have the easiest infrastructure management; however, because of the shared resources, there are higher security risks and a lack of customization.
 A Hybrid Cloud is the combination of two or three of the other cloud types (e.g., on-premises infrastructure and private cloud services maintained on a public cloud). Hybrid clouds can offer great flexibility and scalability, but they are complex and can be difficult to implement.
A Hybrid Cloud is the combination of two or three of the other cloud types (e.g., on-premises infrastructure and private cloud services maintained on a public cloud). Hybrid clouds can offer great flexibility and scalability, but they are complex and can be difficult to implement.
Audit Considerations
As agencies increasingly engage cloud computing services, auditors need a clear understanding of the shared responsibility of security controls between CSPs and stakeholders. This concept is known as the Shared Responsibility Model.
Shared Responsibility – Cloud Security
A common misconception when moving to the cloud, is that the CSP is responsible for safeguarding resources and implementing all security controls. However, the Shared Responsibility Model explains that security is a shared responsibility between the CSP and customer. In a 2020 study, only 8% of Chief Information Security Officers (CISO) understood the Shared Responsibility Model.4 To successfully perform an audit, it is essential to understand the implemented controls, as well as who is responsible for the controls.
The split of the roles in the Shared Responsibility Model between the CSP and customer will vary based on the service model selected. IaaS puts the greatest responsibility on the agency, while SaaS shifts most responsibilities to the CSP. Typically, agencies are responsible for data management and access processes, regardless of the service model.
FedRAMP – The Government Approach5
With increased Federal spending on cloud computing, it was necessary to develop a structured approach for implementing the new services. The Office of Management and Budget (OMB) established FedRAMP in 2011 to provide a risk-based approach for adopting cloud services within the Federal Government. The Federal Risk and Authorization Management Program Authorization Act codified FedRAMP as the official authorization and security assessment for unclassified Federal information on cloud computing. FedRAMP streamlines cloud adoption for Federal agencies by offering standardized security control baselines, as well as templates for contracts and security documentation. The program is required for all Executive departments’ and agencies’ cloud deployments and service models, as outlined above. CSPs offering services to a Federal agency should obtain FedRAMP authorization.
On March 24, 2025 the General Services Administration (GSA) introduced FedRAMP 20x6, an initiative to modernize the FedRAMP program and accelerate cloud adoption across the federal government. FedRAMP 20x aims to automate and streamline the security assessment and authorization process for CSPs. FedRAMP 20x will make authorization simpler, easier, and more cost-effective while continuously improving security. Although FedRAMP 20x represents the future of cloud authorization, the existing Agency Authorization process, based on the FedRAMP Rev. 5 baseline, remains the only active path for obtaining FedRAMP authorization at this time.
As part of the FedRAMP process, during the Pre-Authorization Phase, agencies meet with CSPs to discuss what controls the agency must implement and test. During the Authorization Phase, the agencies design, implement, and test the controls for which they are responsible. This process is documented in a security package that includes a System Security Plan (SSP), which describes the controls in place or planned to meet the security and privacy requirements.
An auditor should consider obtaining the Service-Level Agreement (SLA) between the CSP and the agency. An SLA includes details on the type of service, expected performance levels, and responsibilities assigned, including the controls for which the CSP and agency are each responsible. An auditor can use the SLA to compare the controls documented in the SSP to determine if the entity has the necessary controls implemented.
Examination of Controls at a Service Organization
To support Department of Defense (DoD) financial statement audits, the CSP Security Requirements Guide (SRG)7 requires CSPs and their subcontractors to provide an annual System and Organization Controls (SOC) 1 ®, Type II report. This report demonstrates that management of the CSP’s description of its system is fairly presented, and the CSP’s control objectives are suitably designed and operating effectively. While no similar requirement exists for civilian agencies, it is considered best practice for federal agencies to include SOC 1 reporting provisions in CSP contracts when the system has impacts to the internal controls over financial reporting. Users of a CSP and user auditors, or the auditor of agencies utilizing a CSP, should consider using a SOC 1, Type II report to determine whether agencies can rely on the processes and controls performed by the CSP. In addition to including the processes the CSP performs, the report will enumerate Complementary User Entity Controls (CUEC), which are controls the CSP assumes the agencies have implemented that are necessary to achieve the CSPs control objectives. User auditors must verify the agency has properly designed and implemented controls that address the CUECs.
An Auditors’ Change in Perspective
Auditing in the cloud introduces distinct challenges for both financial and IT auditors, requiring them to navigate a rapidly evolving landscape. To address these challenges effectively, auditors must not only deepen their understanding of cloud services and new data management practices, but also adapt to the shared responsibilities that come with third-party integrations. A key element in this process is maintaining clear communication with the audit client to ensure a shared understanding of the monitoring and testing responsibilities for third-party service providers. As cloud technologies continue to advance, staying informed and flexible will be crucial for auditors to adequately plan and perform audits. Embracing these changes and continuously updating skills will be key to mastering the nuances of auditing within the cloud environment and maintaining the integrity of financial and IT assessments.
Connect with Us
This publication is for informational purposes only and does not constitute professional advice or services, or an endorsement of any kind.
Kearney is a Certified Public Accounting (CPA) firm focused on providing accounting and consulting services to the Federal Government. For more information about Kearney, please visit us at www.kearneyco.com or contact us at (703) 931-5600.
1New Report: Deltek’s Federal Cloud Market Forecast from Fiscal 2021 to Fiscal 2023 – GovWin IQ
2Federal Cloud Computing Spending Trends, FY 2021-2023 – GovWin IQ
3GAO-24-106591, Cloud Security – Federal Authorization Program Usage Increasing, but Challenges Need to Be Fully Addressed
4Oracle Cloud Threat Report – Demystifying the Cloud Shared Responsibility Security Model
5How to Become FedRAMP Authorized | FedRAMP.gov
6FedRAMP 20x | FedRAMP.gov
7Cloud Service Provider (CSP) Security Requirements Guide (SRG), Version 1, Release 2, January 30, 2025
NIST Special Publication 800-145, The NIST Definition of Cloud Computing
Cloud Basics | Cloud Information Center (gsa.gov)
Partners: Cloud Service Providers | FedRAMP.gov